Table of contents
- ✅ What is the operator's username ?
- ✅ What social media platform is the username associated with ?
- ✅ What platform is the cryptographic identifier associated with ?
- ✅ What is the bitcoin address of the operator ?
- ✅ What platform does the operator leak the bitcoin address on ?
- ✅ What is the operator's personal email ?
- 🕵🏼Author : https://twitter.com/mika_sec
- ➡️Pentester at : https://pegasy.co/
Link : https://tryhackme.com/room/adventofcyber3
Difficulty : Easy
Category : OSINT
You are the responding intelligence officer on the hunt for more information about the infamous "Grinch Enterprises" ransomware gang.
As a response to the recent ransomware activity from Grinch Enterprises, your team has managed to collect a sample ransomware note.
!!! ВАЖНЫЙ !!!
Ваши файлы были зашифрованы Гринчем. Мы используем самые современные технологии шифрования.
Чтобы получить доступ к своим файлам, обратитесь к оператору Grinch Enterprises.
Ваш личный идентификационный идентификатор: «b288b97e-665d-4105-a3b2-666da90db14b».
С оператором, назначенным для вашего дела, можно связаться как "GrinchWho31" на всех платформах.
!!! ВАЖНЫЙ !!!
The first step is to translate this note :
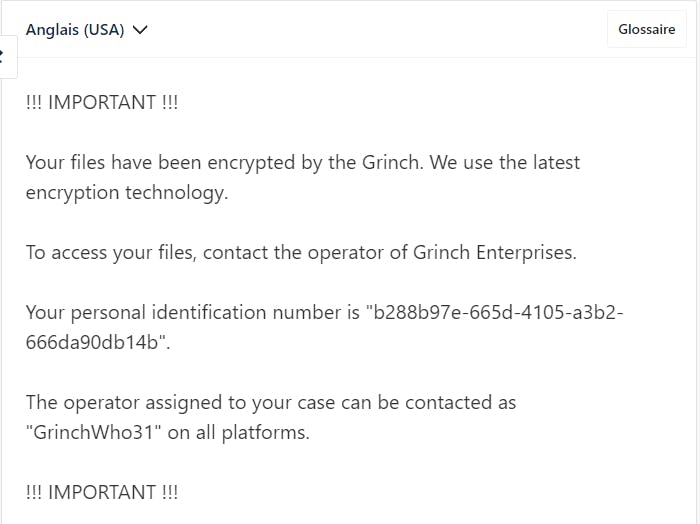
✅ What is the operator's username ?
It is simply in the message translated above :
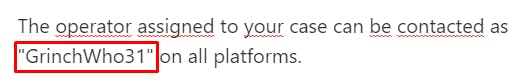
✅ What social media platform is the username associated with ?
Just do a google search for the nickname, the answer is twitter :
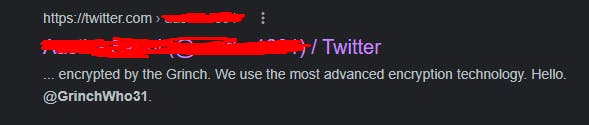
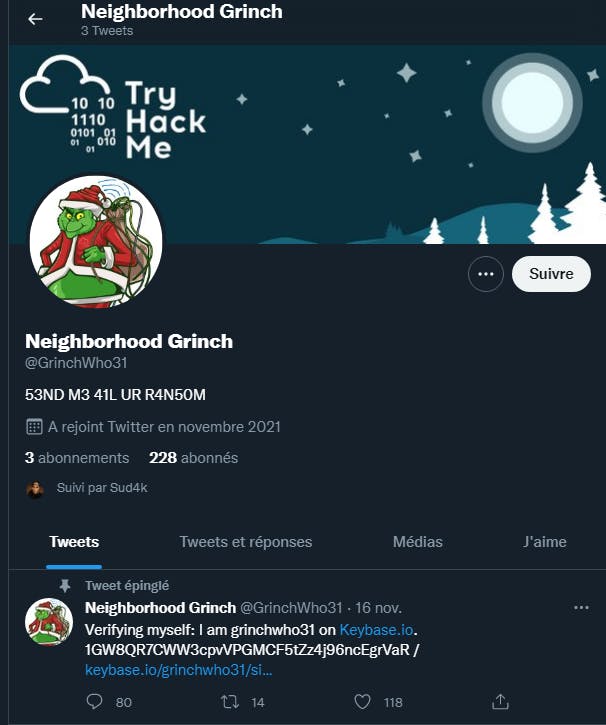
✅ What is the cryptographic identifier associated with the operator ?
The answer is in the one tweet written by GrinchWho31 :
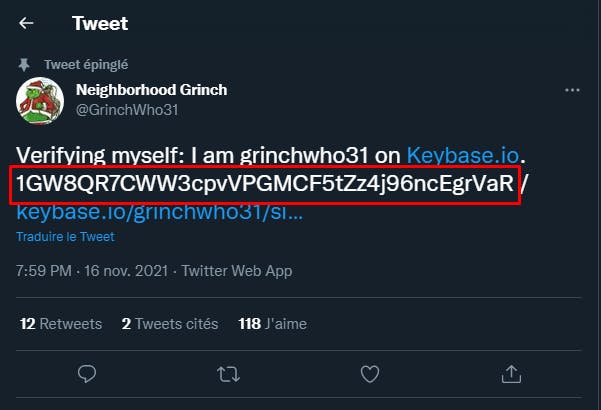
✅ What platform is the cryptographic identifier associated with ?
Same as the previous question, so the answer is keybase.io :
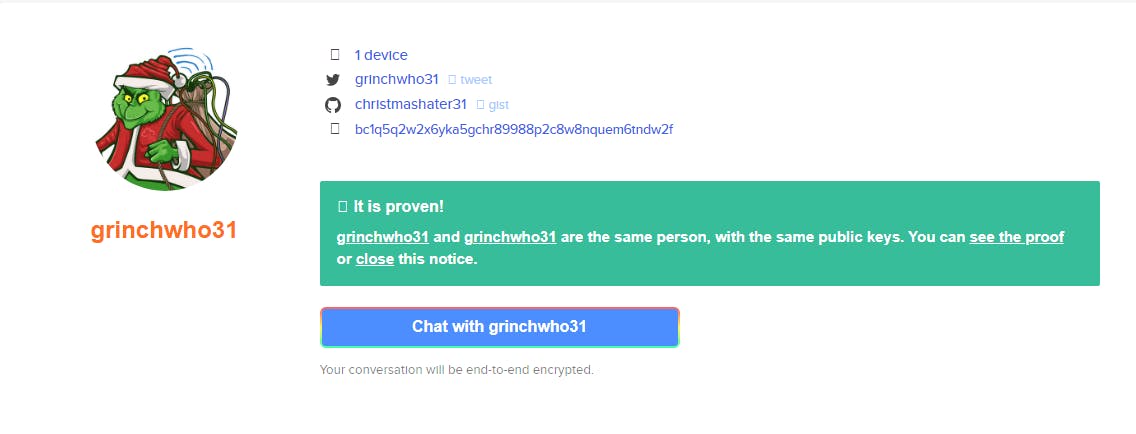
✅ What is the bitcoin address of the operator ?
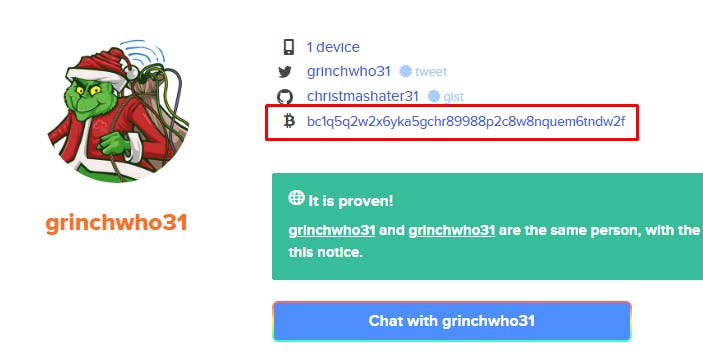
✅ What platform does the operator leak the bitcoin address on ?
This platform is github, the profile is present on its profile keybase.io :
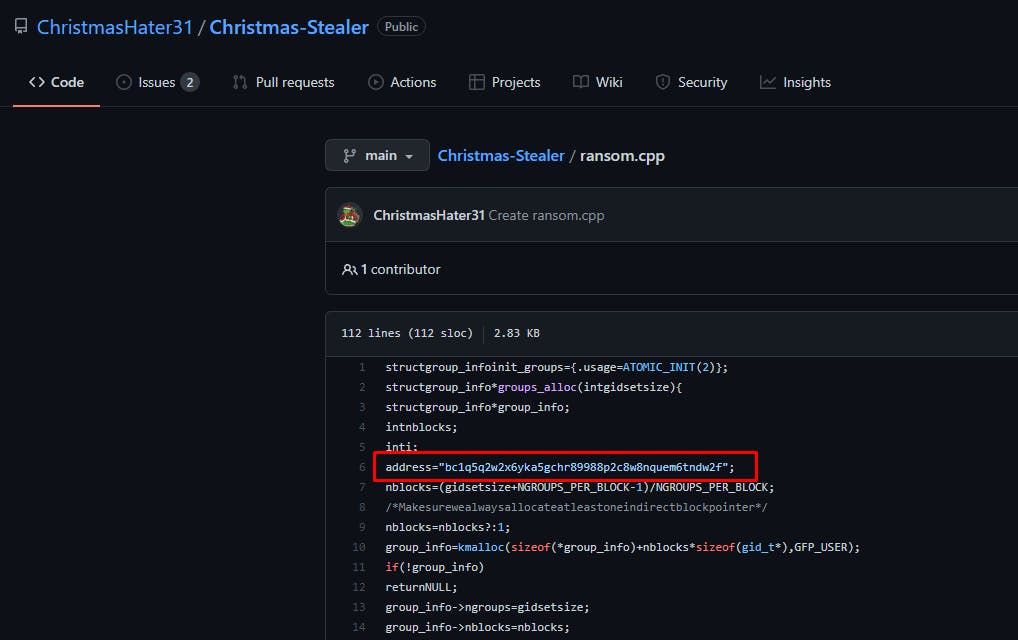
✅ What is the operator's personal email ?
You need to inspect the second repo and look at this commit from November 16 :
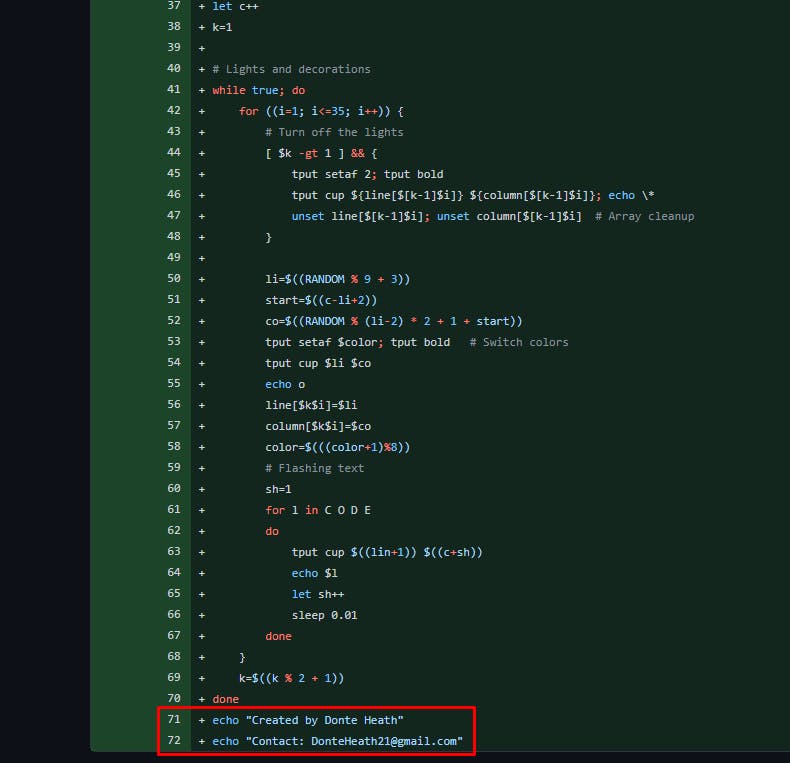
We can therefore also answer the last question of the challenge !
🕵🏼Author : https://twitter.com/mika_sec
➡️Pentester at : https://pegasy.co/


![[TryHackMe] - AoC 3 - Day 16 - Ransomware Madness](https://cdn.hashnode.com/res/hashnode/image/upload/v1640339386138/AIJbE2wFr.jpeg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)